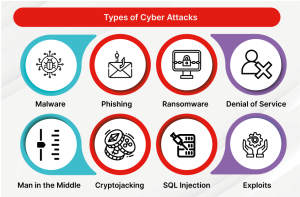
In today's digital age, understanding the different types of cyber attacks is crucial. It helps protect sensitive data and maintain cybersecurity. This article covers some of the most common and dangerous cyber attacks. These include man-in-the-middle interceptions, ransomware extortion, and social engineering.Types of Cyber Attacks Database Injection Attack: Attackers inject harmful code into a database. Often, they use malicious SQL commands to access or alter data. Blended Attacks: These involve a mix of different types of malware. As a result, they spread quickly and cause significant damage. Denial-of-Service (DoS) Attacks: These disrupt communication with a device or crash specific services. Consequently, resources become unavailable to users. Man-in-the-Middle (MitM) Attacks: In this type, an attacker intercepts communication between two devices. They may also insert fake messages during the process. Replay Attacks: Here, attackers resend captured commands to an industrial control system. This approach requires a deep understanding of such systems. Spear Phishing: These are targeted email attacks. They trick users into sharing sensitive information. Although the emails look genuine, they are fake. Social Engineering: This tactic manipulates people to reveal personal information. For example, attackers may seek passwords or account details. Ransomware: Malicious software that locks or threatens to expose data. Victims need to pay a ransom to regain access or prevent data leaks. Watering Hole Attack: Attackers infect websites that their targets visit. As a result, victims unknowingly download malware. Zero-Day Attack: This type exploits unknown system vulnerabilities. Often, they occur before developers can fix the issue. Conclusion: Cyber attacks are becoming more advanced and harder to detect. Therefore, knowing these common types can help individuals and organizations stay safe. By staying informed and vigilant, it is possible to improve security and reduce risks. Image credit: fortinet

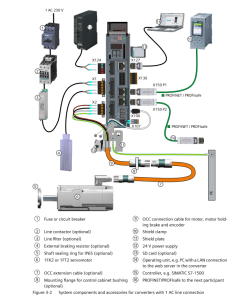
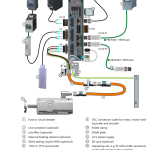
Control Panel Design
Short-Circuit Current Rating (SCCR) for Control Panel
In industrial automation and control system design, Short-Circuit Current Rating (SCCR) is a critical safety parameter. It defines the maximum short-circuit current that an industrial